We launched Arm System Design Kits with a simple goal—to make it easier, cheaper and faster for designers to build secure SoCs. The demand for smart, connected products has been growing rapidly, and so has the variety and complexity of IoT applications. Our System Design Kits have been evolving to support more advanced applications, such as machine learning at the edge.
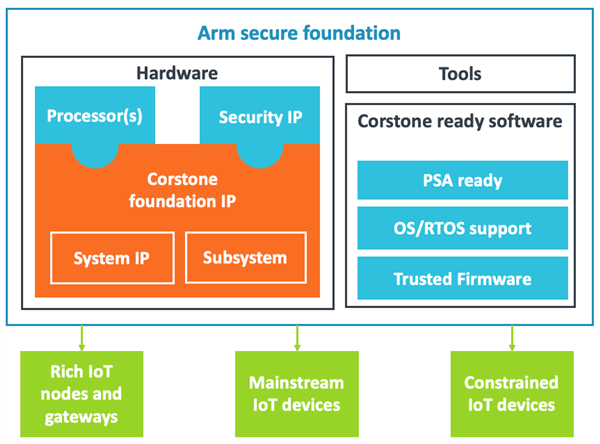
To reflect the growing complexity and variety of IoT applications, and to answer the need for a complete system approach, we are introducing a new umbrella solution called Arm secure foundation, and a new brand to replace the System Design Kits: Arm Corstone foundation IP.
The goal is to provide a foundation built on the Arm Platform Security Architecture (PSA) principles, that our partners can extend and differentiate for a diverse range of end applications. This secure foundation brings together the necessary hardware, software and tools to accelerate product development, reduce risk and importantly, enable software development on a standardized architecture.
In the future, will everything be smart and connected?
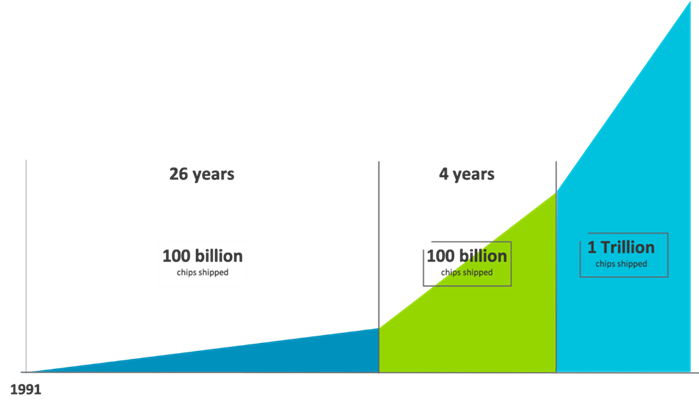
The IoT world is growing at a breath-taking pace, with one trillion devices projected to be in use by 2035.
The increasing diversity and complexity of IoT applications creates more challenges to SoC designers, and these are no longer limited to time and cost. More complexity means significant integration and validation effort, huge investments, and extensive engineering resource requirements with high-level skills. Security can no longer be an afterthought and implementing it is becoming more and more complex too, as the scale of the systems makes them harder to protect against attacks.
Designers must also grapple with device specific requirements which vary significantly across device types, from a low cost ultra-constrained sensor to a high performance edge gateway.
For example, a temperature sensor would require very limited processing abilities whereas a smart security camera may need significant processing capabilities at the edge for object detection before sending alerts to the cloud rather than sending every frame of video.
| Rich IoT nodes & gateways | Mainstream | Constrained |
 |  |  |
|
|
|
Challenges vary across types of devices
For IoT to scale up, we need solutions instead of individual pieces of IP. Furthermore, we need to provide designers with the right solutions for their type of device; solutions that address their application requirements in a targeted way, whilst helping to speed time-to-market, reduce overall cost and ensure system-wide security.
Why Arm secure foundations?
We believe that such a solution-based approach can add real value to our partners. That’s why we have created the Arm secure foundations, tailored solutions for jump starting secure PSA (Platform Security Architecture) ready SoC designs. Matched against the main IoT application classes, they facilitate a more efficient approach to designing a secure SoC, by addressing the key challenges specific to the application type and giving access to a software ecosystem that is already prepared to make use of the hardware security features and bring security to the IoT devices.

Each solution builds on Corstone foundation IP, development tools (e.g. FPGA) and Corstone ready software for a complete system approach.
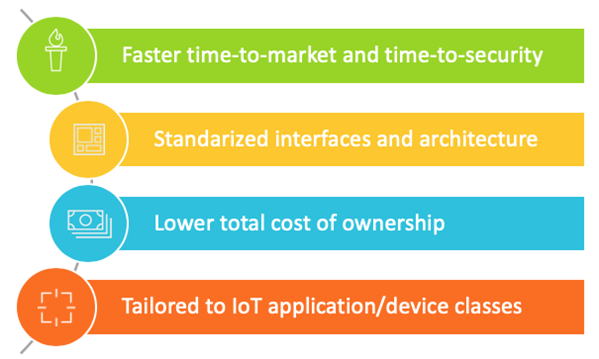
The key IoT system ingredients are provided to reduce time-to-market: essential system IP, pre-verified subsystems, evaluation systems, supporting documentation, low-level software and even the entire IoT firmware frameworks like Mbed OS, adapted to the subsystems. Flexible, modular standards-based architectures support multiple IoT use cases, thanks to highly configurable system IP and modifiable subsystem IP. SoC designers can benefit from an ecosystem using common software elements to reduce risk and cost.
As security cannot be an afterthought, it is taken into account from the system architecture definition and pre-built into the subsystems, using the PSA principles and integrating security IP like firewalls, secure enclave and TrustZone technology.
Instead of designing the compute subsystem architecture and assembling all the elements by hand, SoC designers can now focus on diversity and differentiation for their businesses to thrive in new IoT applications. This leads to faster time-to-market of more diversified solutions.
OK, but what is Corstone?
Corstone is our new brand name for System Design Kits. At the heart of Arm secure foundations are Arm Corstone foundation IP, which include highly configurable system IP and pre-verified subsystem IP, pre-integrated with the processor and security IP. Think of Corstone as the cornerstone on which a great building, or in this case, IoT application, is built.
The wide range of end applications require a different class of secure foundation.
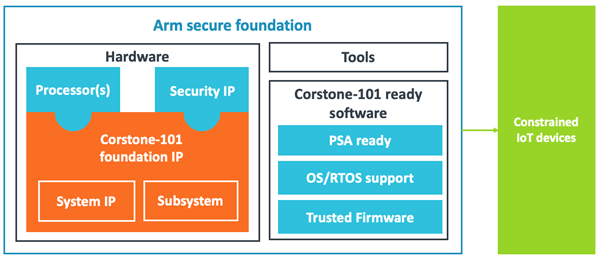
Constrained Systems
Corstone-101 foundation IP is an essential design kit with a first level of security as it provides the minimum hardware element needed in secure systems: a true random number generator (TRNG). This IP is essential to seed all the cryptographic functions and cannot be replaced by the software. However, other elements of a secure system will have to be built manually.
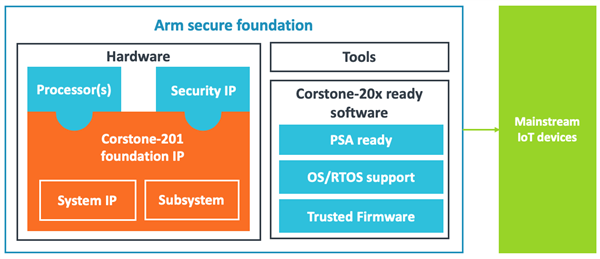
Mainstream systems
Corstone-201 foundation IP solves this problem by using the TrustZone technology and supporting the latest Arm Cortex-M processors. It also contains all the elements of the Corstone-101 foundation IP, in addition to a Cortex-M33 based subsystem and a Cortex-M23 subsystem example, generic flash controllers, secure debug solutions, and power control elements.
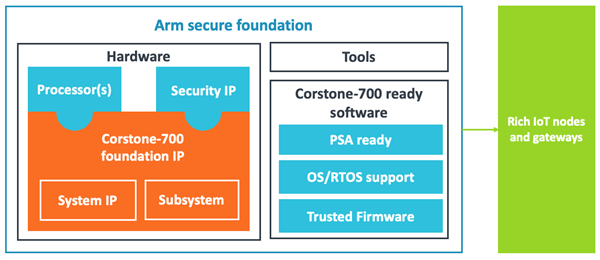
Rich IoT node and gateway systems
Corstone-700 foundation IP combines Cortex-M and Cortex-A processors in a powerful flexible subsystem with many security features, including firewalls to protect the heart of the system. It supports extension ports for high-speed peripherals like media engines or neural processing elements, and can host several M-Class components to address different requirements.
Another component of the Arm secure foundation solution is Corstone ready software built upon open source software elements that complement the subsystems perfectly, speeding up product development. With a goal of proven bootloaders, drivers, HAL and example applications running out of box, it offers compatible software solution to support Corstone foundation IP. Special Corstone ready versions of Mbed OS are also available to provide as many useful resources as possible to embedded software developers and make it very easy to create a complete software to manage their devices.
To learn more about Arm secure foundations and Corstone foundation IP, please visit Corstone Foundation IP or contact us with any questions.
Learn more about secure foundations and Corstone foundation IP
Leave a Reply