This month we celebrate the first birthday of the Arm Platform Security Architecture (PSA) and with any special birthday, it’s a great time to look back and reflect on the year that’s passed.
The Arm Platform Security Architecture was created to ease some of the pain points surrounding security development, offering a common framework for building secure devices. It introduced three key stages of security design and technical resources to make security simple, even if you’re not a security expert. Let’s take a look back over the key milestones that made PSA so exciting this year.
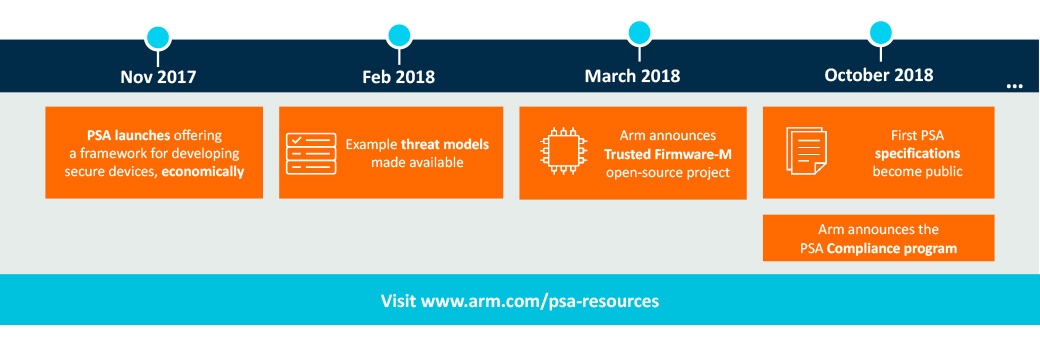
Fig.1 PSA milestones
Threat Modeling becomes simpler
The first stage of PSA (and security design, in general) should be to assess the value of your data and the threats your device may face. It’s a process well documented as “Threat Modeling and Security Analyses” and has been used widely in the mobile industry for a long time, where you may have seen them referred to as Protection Profiles. For many IoT designers, this process is brand new and can feel a little daunting – which is why, in February, we released three example threat models. The threat models analyze three common IoT devices (a smart water meter, a network camera and an asset tracker) and guide you through the entire process including:
- What does the device do? What are the key features?
- What are the important assets of the device? What user data is collected?
- What security threats might the device face?
- What subsequent security objectives are needed to make the device more secure?
Threat Models are a key part of PSA and we are proud to offer them to the industry. Learn more about the Threat Modeling and Security Analyses documentation.
More partners join the effort
Securing the Internet of Things (IoT) is not something that one company or entity can achieve alone. In fact, at Arm we believe that security is a shared responsibility and should be embraced by the whole ecosystem, from chip to cloud. It’s the responsibility of the whole ecosystem to ensure that connected devices communicate a common secure foundation.
Since the birth of PSA, we’ve spoken a lot about partnership and we’re proud to work closely with a number of PSA partners; a set of relationships that have grown over the last 12 months. The list of partners continues to grow and includes leading cloud, hardware, and silicon providers, with many of the biggest names in the industry endorsing and/or supporting PSA and the principles it is based on. Some great examples of PSA partner collaboration include the Cypress Semiconductor whitepaper and the Trustonic webinar.

Fig.2 PSA Partners
Architectural documentation brings PSA to life
Underpinning PSA is the range of technical documentation and specifications, which outlines the thinking and priorities within security design. It’s something we’ve been working on for a long time with our PSA partners, so we’re pleased that it’s now available in the public domain for the rest of the security ecosystem. There are four key documents that bring PSA to life:
- The PSA Security Model: starting with 10 key goals for designing devices with known security properties, the PSA Security Model outlines important details for deploying secure services.
- Trusted Boot and Firmware Update: outlines the technical requirements surrounding firmware boot and update.
- Trusted Base System Architecture for M: possibly the most useful document for chip designers, offering detailed hardware requirements for Armv8-M based devices (plus some recommendations for Armv6-M and Armv7-M based devices). It even has a handy checklist of things to consider at the back of the document.
- PSA Firmware Framework (PSA-FF): a standard programming environment and fundamental Root of Trust (RoT) security services.
Practically speaking, the specifications are the quickest and easiest way to get started with PSA. Head to the PSA resources hub to download them and start reading.
Support for software developers
If you’re looking to develop secure code, we also have you covered. At Arm, we recognize that as IoT security becomes more complex, the ecosystem needs a reference implementation firmware. Trusted Firmware-M is exactly that! Trusted Firmware has been around for a long time, supporting A-Profile devices but has recently turned its attention to M-Profile devices. It offers a completely open-source reference implementation firmware that conforms to the PSA specifications, which makes development easier, quicker and cheaper!
We strongly encourage you to visit the Trusted Firmware website and get involved with Trusted Firmware-M (by downloading the code and helping to develop the program), especially if security on resource-constrained systems is important to your company.
On top of open source code, Arm also offer the chance to develop using our Musca-B1 platform. You can learn more in this blog on the Musca-B1 test chip.
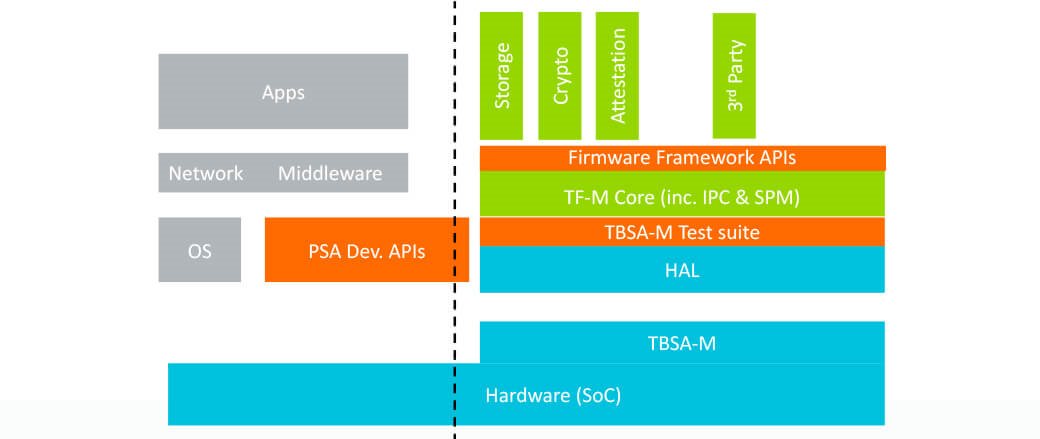
Fig.3 New APIs will accelerate development cycles
Accelerating development with functional APIs
Now for the latest news of the year – the availability of PSA APIs. Arm has just announced the beta availability of PSA APIs and corresponding API testing kits, which offer PSA partners the opportunity to accelerate development cycles. The APIs and test kits look at three areas of design, including: PSA Developer APIs for RTOS vendors and software developers, PSA Firmware Framework APIs for security experts making custom secure functions, and TBSA-M test kits designed for chip vendors (which checks for the hardware against the PSA TBSA-M specification).
If you’re interested in exploring these new APIs and API testing kits, check out the web page for more information on how it works.

Fig.4 PSA One Year On
It’s not over yet…
It’s been a whirlwind twelve months but an exciting journey for PSA and the Arm ecosystem. It’s a journey that isn’t over yet – you can follow the journey by signing up for email alerts. Everything you need regarding PSA and its holistic set of resources, can be found on the PSA resources page below. IoT security remains an important topic and it’s something that will continue to grow and adapt. As always, Arm and the Arm Platform Security Architecture will be monitoring the trends and responding, to help secure the Internet of Things.
Leave a Reply