The insecurity of IoT systems is a widely known and discussed problem and continues to drive decision-making for system designs throughout the ecosystem. The Arm Platform Security Architecture (PSA) is being developed to address this challenge and make it easier and quicker to build trustworthy systems. We propose that all chips, even low-cost microcontrollers, should have some level of hardware security to isolate secure services away from the rest of the system.
Hardware security and PSA Root of Trust (PRoT)
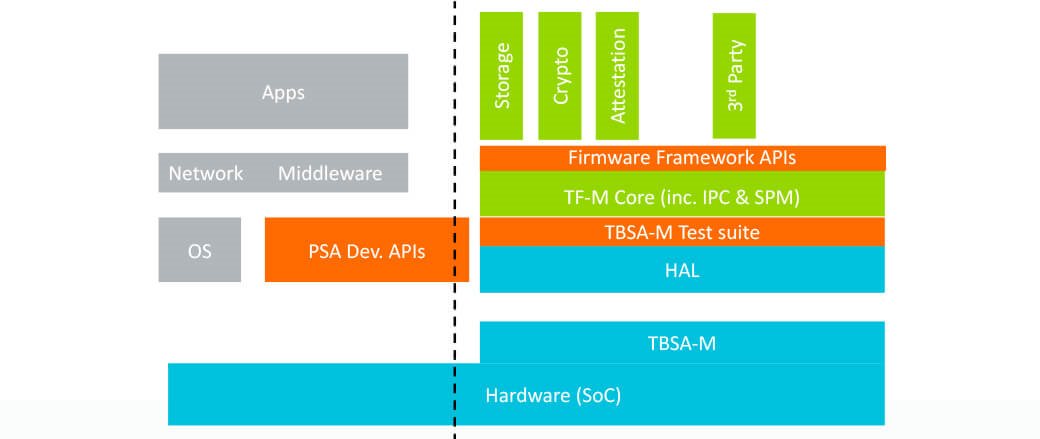
PSA provides a set of architecture documents to standardize the fundamental security system and services as the PSA Root of Trust (PRoT). There are many ways a chip vendor could construct a good PRoT, they could for example: use a processor with TrustZone hardware isolation, add in a security subsystem such as Arm CryptoCell or opt to dedicate a small microcontroller to provide the isolated secure services. Arm has published a hardware requirements document called Trusted Base System Architecture-M (where M stands for microcontroller), which provides recommendations to chip vendors for multiple different implementation choices that could be used to create a PRoT. The chip designer will look at their target markets, choose an implementation pattern and integrate trusted software to create a PSA system. To make the development process even easier and quicker there is an open source, open governance project (Trusted Firmware-M) that provides a reference implementation.
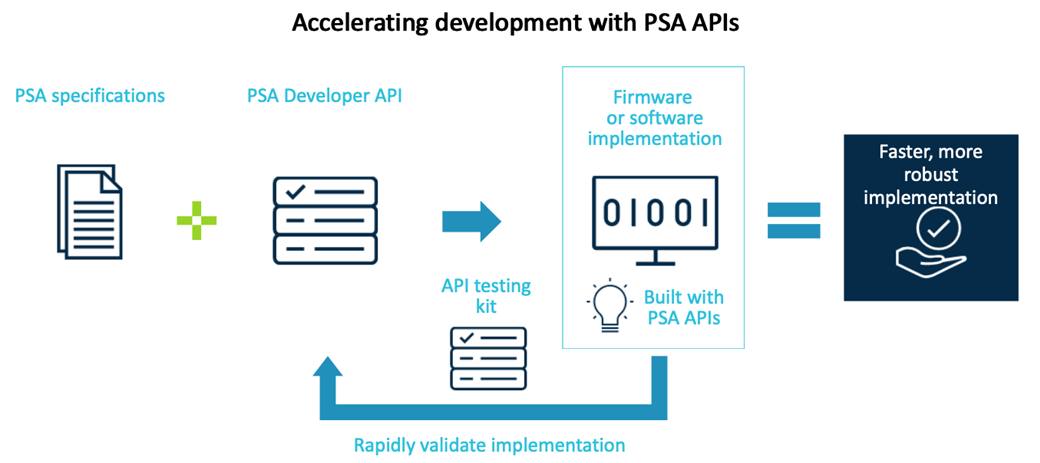
New PSA APIs will ramp development cycles
To mask underlying hardware differences, we need some APIs that can provide a consistent developer experience across different chips and platforms. Arm has created three sets of APIs with API testing kits aimed at different developer communities. Together they enable efficient development of software, security functions and hardware.
- PSA Developer APIs are the top-level APIs used by application developers and RTOS vendors. These APIs have been designed to be used by software developers who wish to use the hardware security features without necessarily being security experts themselves. These APIs provide the top-level essential services of: crypto, secure storage and attestation tokens. The open source Trusted Firmware-M project is developing a reference implementation. At the time of writing Crypto APIs are already publicly available with Secure Storage and Entity Attestation Token to follow soon.
- PSA Firmware Framework APIs are designed for developers of secure functions (aka Application Root of Trust Services or ARoT). Security experts wishing to add their own security functionality can develop an AROT service that can be used on different chips using these standard APIs.
- The TBSA-M API Kit enables chip vendors to check the functionality of their chips against the proposed hardware requirements checklist contained in the Trusted Base System Architecture-M document.
These APIs, corresponding API testing kits and the PSA architecture documents that underpin them are architecture agnostic; there is no specific Arm technology required.
Show me the code!
Trusted Firmware-M is an open source, open governance project hosted by Linaro on Trusted Firmware. You will find early versions of the APIs there and we would like your feedback before they become Beta early in 2019. As an example, have a look at our crypto libraries that are based on the successful crypto libs in Mbed TLS.
Some of the PSA API testing kits are also available via GitHub.
How do I get started with PSA?
Download the architecture documents to review the Security Model and Firmware Framework. If you are a chip designer also download the Trusted Base System Architecture-M for proposed hardware security requirements (there is a useful checklist at the back). The testing kit accompanying TBSA-M can be found on Github.
If you are an IoT developer or RTOS vendor look on trustedfirmware.org for a range of available APIs and reference code, we plan to have all APIs at Beta quality by January 2019, so if they are not there today please keep checking from time-to-time. If you want to find out more about EAT and how it can be used for devices to make standardized claims please follow the conversation in IETF.
If you are looking for a platform to begin developing secure code, take a look at our Musca-B1 platform.
Finally, if you are a security expert wanting to develop your own secure functions (Application RoT Services) we encourage you to look at the Firmware Framework APIs and our example secure services.
Leave a Reply