The facilities industry is making it clear to us at Arm that they are increasingly focused on their assets, which are the inhabitants and objects located inside their buildings. Importance is being placed on the use cases that are making people happier, more productive, secure, and more comfortable. Smart lighting has been an exciting topic for Arm, because it is a very convenient backbone for all the insights that should be collected from a connected space. By necessity, lighting is found everywhere – from the parking garage to the IT room – and the digitization of solid-state lighting has facilitated the production and transmission of relevant data from lights, turning them into very powerful conduits for all the information that the facilities owner or operator would need from the building.
With people spending 90% of their time indoors, and a large amount of buildings’ operating costs being the lifetime costs of energy, gaining these types of insights becomes critical for not only the management of real estate but also considerations like employee retention, employee attraction, improving the asset value, security and safety of the building, as well as increasing the convenience levels of the inhabitants. We see that the future of smart lighting will offer countless benefits, from space optimization and asset visibility to office security, wayfinding, object detection and building automation.
How Arm is tackling smart lighting
Arm’s point of view is that, by harnessing the intelligence provided by the Internet of Things (IoT), it’s possible to make buildings more sustainable, more secure, and responsive to internal/external stimuli. Arm’s background is ideally suited to offer innovative IoT solutions, with a legacy in architecting new technologies in a variety of markets, including smartphones, advanced sensors, development boards. By combining our strength in hardware and some of our new software and services on offer, assisting in the deployment of smart lighting solutions is a natural next step for Arm.
Arm is pervasive across the smart building architecture
Arm technology is found throughout the smart building ecosystem, especially in areas supported by miniature low-power sensors: thermostats, lighting controllers and more – devices which have been one of Arm’s strengths for many years.
Focus on developing applications, without worrying about the rest
The industry has dictated a very clear and concise list of requirements in smart lighting:
- Easy development and deployment
- No lock-in (device, connectivity, cloud)
- Robust device-to-cloud security
- Interoperability with other systems
- Worry-free device lifecycle management
- Connectivity abstraction and management
- Seamless data ingest and analytics
An ideal platform would offer transparent connectivity abstraction to easily be built upon, so that an IoT developer, or a smart lighting developer only needs to concern themselves with creating an application in the cloud or maybe, for an embedded engineer, creating an application on the device. All the factors in between, such as the connectivity protocols, whether you need a gateway or not, deciding between a cloud solution or on-prem, whether you need access for maintenance and commissioning when there is no connectivity available, should be easily handled by the platform.
Lighting OEMs are also interested in avoiding vendor lock-in, whether it’s in respect to the cloud, technology stacks or the hardware itself. They’re also interested in ensuring high levels of security throughout the deployment.
Security: One of the biggest considerations in smart lighting adoption
Despite forecasts of large growth within the market, in actuality many decision-makers are shying away from implementing a smart lighting solution. Security concerns are one of the largest reasons cited for this hesitance.
A trusted, secure foundation is essential for developing IoT devices. A single vulnerability that may arise from the smallest of sensor devices in a deployment can create havoc, from bringing down the grid to sending out spam messages to cripple a network.
Securing the critical foundation of smart lighting
A lighting vendor or developer or engineer should be focused on the factors that they’re able to derive value from, such as the items at the top of the pyramid above. They want to build excellent applications for their customers that help them with office security or wayfinding or asset visibility or improving building automation. Everything under the hood, whether it be hardware at the bottom-most layer, or the connectivity stacks, or even security considerations such as secure boot or secure software updates, should typically be taken care of and secured from the chip to the cloud.
For true security, just providing the basic building blocks is insufficient. These blocks, which may be built in-house, found in an opensource GitHub, or even licensed from another company, might consist of a variety of security options like a secure factory tool or a threat analysis model or a mechanism for firmware updates over-the-air. Just combining these ingredients will not be enough – security must be considered at the system level.
Arm addresses these concerns through a rigorous security process, starting from the smallest of crypto-libraries in the chip to a secure communication channel that is encrypted. Security must be built from the ground up and at the core of every device. There is also no single point of ownership for security; the whole IoT value chain needs to share in that responsibility and seamless security should be pervasive, from the foundational architecture to the cloud service.
The 4 pillars of Platform Security Architecture
Arm’s Platform Security Architecture, which was announced in 2017, provides a recipe for creating a secure system as well as a reference implementation.
Arm PSA was developed with security consultants, based on a thorough analysis of several IoT devices and the threat vectors that could cause vulnerabilities
PSA addresses security concerns for any device, even the most constrained processors. By considering the different attack surfaces that need to be protected, threat profiles can be produced and the appropriate architecture for hardware and firmware is recommended.
The common principles identified, across many use cases:
- An immutable device identity which bolsters integrity: Identity should be set inside the chip using true random number generators and cryptolibraries.
- Trusted boot sequence: Builds the integrity and develops it from the moment the device (such as a smart lighting controller) wakes up, it needs to access a secure area where it can get the rest of the boot code and operating system.
- Secure over-the-air update: Over the whole lifecycle of the device, it will be necessary to securely process OTA updates.
- Crypto-based authentication: Certificates allow much stronger levels of security, compared to just using encryption.
PSA is key for secure smart lighting
The smart lighting industry aligns closely to the key principles of PSA. Arm is working closely with a variety of companies from the industry to build out these threat models and implement the security architecture. Everything, from the secure device identity located in the sensor and microcontroller inside a luminaire, through to the trusted boot sequence and further on to secure OTA update, goes beyond pure encryption. Communication channels are secured through TLS; all the firmware updates are done very carefully through an update program, with manifests and certificates. All of these elements are critical “spokes in the wheel”, they are all necessary and never optional.
When assessing the level of security that must be built in to the system, there are a variety of threats to be considered.
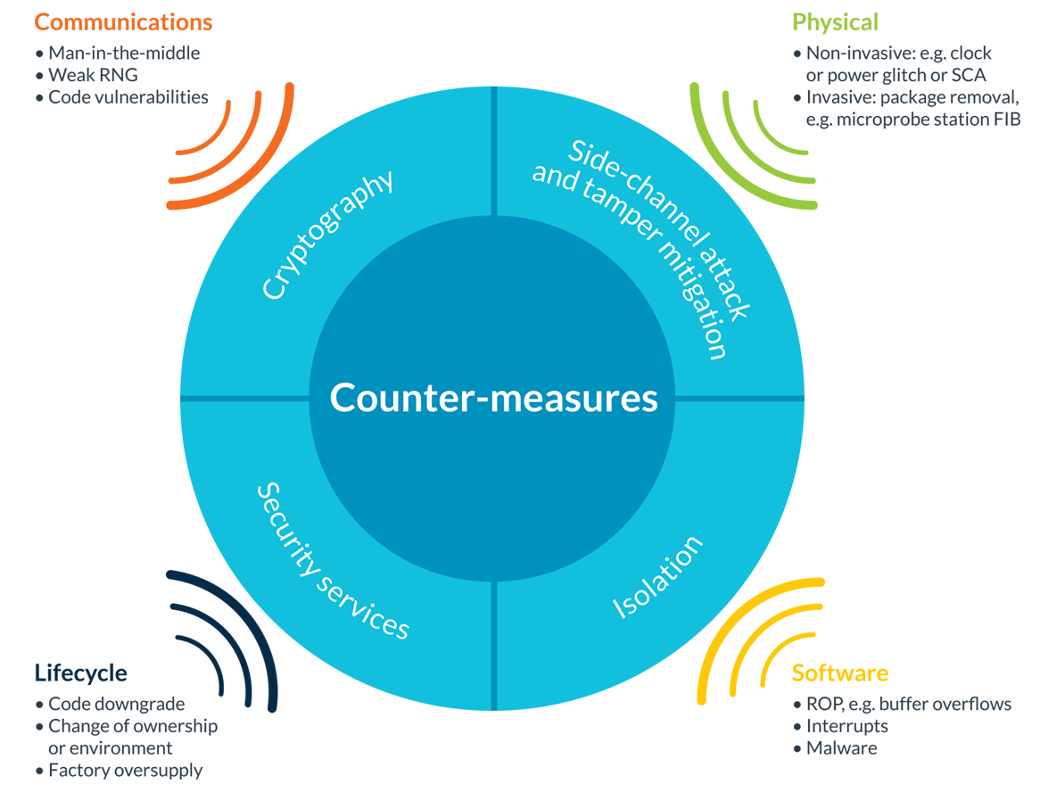
Potential threats and countermeasures
Security is being used to address a variety of vulnerabilities, everything from hardware blocks to software modules.
The image above covers four types of issues:
- Communications: Every IoT device has a mechanism for connecting to the cloud, which means that every time it connects, there is a communications channel that could be exploited. The common solution for this has been encryption, which secures many of these channels.
- Lifecycle: The integrity of the device must be protected during its lifecycle, as it changes hands many times during the move from the factory to the end-user’s ongoing operation and on to the end of its life. Common attacks such as a downgrade of the device’s code to a more buggy or faulty version may allow for unauthorized access to device data. Mechanisms like anti-rollback measures can be built in to avoid these types of threats.
- Physical: If your data is truly valuable, hackers may resort to physical means of extracting data. For example, they could breach the plastic covering of the device and insert probes in the circuit to access information that is common to all devices in that batch.
- Software: Existing code could be buggy or may be attacked via malware; a secure solution should specify which sorts of attacks must be protected against.
A security analysis helps to identify the different threat vectors and surfaces, but it also prompts the question of “How much security is really enough?”. Someone stealing temperature reading data from a thermostat may not be considered a huge threat, but if a hacker gains access to the controls of thousands of sensors and sends random messages through the network to bring it offline, there is a major issue with the system.
The security analysis should begin with a complete system description then consideration of the assets which need protecting and potential threats to those assets. Next step is to establish the security objectives and the requirements needed to meet those objectives. This analysis will result in a solid threat model and security architecture.
A smart lighting example:
- Asset: Smart lighting data produced by sensors must be protected in integrity and confidentiality
- Threat: Remote software attacks
- Security objective: Strong crypto protection
- Security requirement: Hardware-based key store
Securing each stage of a smart lighting device’s lifecycle
Addressing security concerns across the entire lifecycle of a device
Not only is it important to establish threat modelling and a security analysis, we must also consider every stage of the device lifecycle and address threats during each phase, from manufacturing through on-boarding and regular use to the end of life.
From the moment a device is built, mechanisms must be in place at the factory level to provision all the secrets and keys into the device.
When the device wakes up, bootstrapping should happen securely. If the device changes ownership, then mechanisms like first-to-claim commissioning will secure that process. Consider also certificate authorities, either third party or in-house.
Finally, during regular use and end of life, secure software updates must be managed, and when there is a lack of connectivity, there should be a mechanism to allow for secure access of the device.
For more in-depth information around security for each stage of the device lifecycle, watch our webinar: ”Secure Smart Lighting: Unlocking a building’s IoT potential”.
Conclusion
When we consider all the factors addressed in this blog post, it becomes clear that security is an important cornerstone of smart lighting, which may be preventing the industry from truly unlocking all IoT potential inside a building. Progress is being held back because of concerns in security. The industry and ecosystem can ensure that each IoT device deployed is also secure, from the smallest of sensors to a lighting controller to a switch to a Linux-based gateway box. The mechanisms that we have discussed are ways in which we make the device trustworthy, ensure a trusted anchor, ensure that the lifecycle operation of the smart lighting device is secure, the communications channels over which data is sent to the cloud is secure, and that during the lifecycle, all the updates are done in a robust, secure way. These features provide security from the foundation of the device, through to the cloud and beyond.
Leave a Reply