Cyber-threats are growing every day and what traditionally was seen as a data protection issue in the IT domain is becoming an increasing reality in the machine-to-machine (M2M) domain. Compounding this rise in capability is the rapid growth of the Internet of Things (IoT), writes Robin Duke-Woolley, the chief executive of Beecham Research. In this fast moving market we are becoming increasingly connected, whether through cellular, Wi-Fi, bespoke wireless or other connections. This interconnection inherently creates a massive expansion in the attack surface available to hackers. Couple this with new devices being rapidly developed and deployed to market, with all of the inherent code issues and bugs in new products and there is a golden opportunity for attackers.
Traditionally, control and monitoring systems were isolated or of limited interest to attackers. Today we are moving to a place where smart meters enable utilities to monitor, and ultimately control or kill, power to a house, potentially enabling a burglar to either monitor if a family is at home or on vacation, or maybe even switching off the electricity prior to committing a robbery. We are seeing smart white goods developed with good intentions to allow smoothing out of electrical peaks on the power grid, but which again could be used to build up a picture of an individual’s habits or movement. And, of course, we are seeing the creation of complex industrial control systems that have been compromised through a variety of attacks. In other words, the capability to attack M2M systems has expanded at the same time as the value of such an attack is increasing and has been demonstrated.

Robin Duke-Woolley, CEO Beecham Research
With the move from strongly and simply architected M2M systems to more fluid IoT solutions this attack surface, and the realistic ability to do significant harm, is set to accelerate. This means it is very important that the industry as a whole joins together to architect the IoT for security from the ground up to ensure the right frameworks are in place. This must ensure innovation and security is implemented without the need for massive and expensive layers of software and services that are ultimately debilitating to the usability and economics of the IoT solutions.
All IoT stakeholders have a part to play
The security issues are systemic and ultimately rely on all stakeholders working together.
- End users must develop the capability to measure and manage risk, enabling them both to manage their long-term business and to enable formal liabilities to be assessed.
- System integrators must be able to build, test and certify systems against current and future unknown attacks. System integrators must assume responsibility for consumption of complex technologies for multiple vendors and need to balance security inside a system architecture.
- Original equipment manufacturers (OEMs) need to design better devices to reduce system integration issues and software complexity. Devices must include relevant security features including next generation antimalware solutions and policy management capabilities.
- Silicon vendors must ultimately put in place the fundamental building blocks to strongly root security and enable functionality in an easily consumable framework. Security will always be device and use-case specific and will vary in capability across secure elements (SIM-type devices), smart sensors, microcontrollers and microprocessor/system on chip (SoC) devices found in gateways and networking applications.
To enable a safe, secure and robust IoT it is critical that security is achieved from end-to-end, from the servers and cloud services that are subject to traditional IT security measures all the way to the vast number of edge nodes that will evolve over the next decade.
To achieve the level of security required, an evolution in the capability of most devices is needed to deliver robust architectures that maintain simplicity for the user.
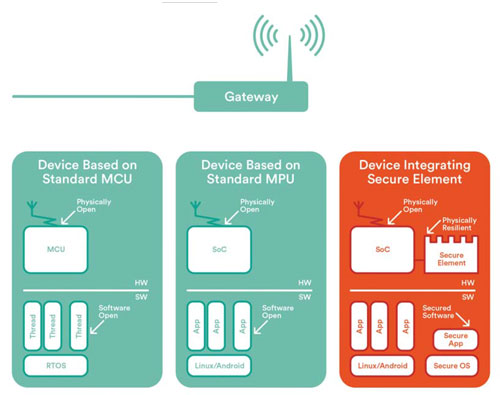
Figure 1: Existing IoT device classifications
The silicon level
IoT will continue to be defined by a vast array of different solutions, varying from extremely low cost to extremely complex devices, and from single remote nodes through to autonomous mesh networks. As such there is no single answer for what a device should look like. Instead, it is useful to explore the security challenges within IoT through three existing processor hardware categories:
- Secure element
- Secure microcontroller
- Secure microprocessor
1. Secure elements
These devices are at the forefront of many M2M systems as embedded subscriber identification modules (eSIMS) in connected cars, new smart meters and other areas.
- Strength: IoT secure elements inherently utilise security features designed for mobile SIMs, and therefore can easily meet the basic IoT security certification requirements. Today, the secure element is the favoured approach to embedding security within devices either as a traditional SIM or an embedded SIM.
- Weakness: Secure elements typically have strictly limited functionality and are therefore useful for creating a trusted point within a system. However, the target application, such as monitoring and control, must exist on a separate processor increasing costs and reducing system security.
2. Secure microcontroller
Microcontrollers (MCU) are the traditional workhorses of the IoT offering relatively low cost and fast time-to-market with strong tools ecosystems and high levels of ease of use. However, MCUs have not traditionally been designed with a robust root of trust and security in mind, and as cyber-threats grow vendors are needing to react to this requirement.
Some vendors, especially of 32-bit MCU devices, have introduced some security requirements. For example, many vendors now include cryptographic accelerators, such as advanced encryption standard or secure hash algorithm (AES/SHA), and some include special tamper-resistant pins on the microcontroller to detect if the device’s external box has been compromised. However, these devices are still open to significant attacks and could represent vulnerable points to inject viruses or compromises to systems.
- Strength: The vast array of microcontrollers, and their ability to easily integrate cyber-physical requirements through their specialist interfaces, makes MCUs the mainstream platform for IoT nodes.
- Weakness: The limited security capabilities of microcontrollers are the biggest limitation of these devices within the IoT domain. While more and more MCUs are integrating encryption and decryption capabilities, there is little standard behaviour beyond that to secure the system against the growing cyber risks.
3. Secure microprocessor
The cost of high performance microprocessors continues to fall as strong competitive pressures and oversupply impact the mobile handset marketplace. Devices that traditionally cost more than US$20 are now retailing at an entry level of sub-US$5 in volume, delivering unprecedented price to performance ratios.
The positive impact of price-constrained microprocessors (MPUs) is that many more of these devices can be deployed into a wide array of M2M and IoT devices ranging from the traditional router or gateway down to relatively inexpensive edge devices. Indeed, many of the pioneering, mainstream IoT devices such as the Nest Thermostat are based on such microprocessors.
The nature of these MPUs is that they have traditionally been designed to run rich operating systems, such as Android, Linux and Windows, which offer great flexibility but a limited approach to security based on memory management unit (MMU), and virtualisation to create application sandboxes.
For additional strength against advanced and persistent threats, some processor vendors have added specific processors to their SoCs, either with complete fully fledged processors with complete memory systems, or via virtual processors, one of the most well-known of which is Arm’s TrustZone technology.
The advanced process geometry and cost of large SoCs have meant these devices tend to have limited on-chip storage memory, with execution random access memory (RAM) on device and off-chip flash supporting execution code. This approach, while cost efficient, does lead to a requirement for specific secure boot processes, and the use of secure elements for critical control points or data.
- Strength: The wide array of performance points and modern vendors of SoC type devices has led to a rich variety of chips that can be utilised widely. While the majority of devices utilised in IoT were originally conceived for mobile type applications there is a good synergy in terms of cost, power and ability to execute many applications. Further integration of some security technologies has led to the emergence of a small but robust ecosystem of software vendors which support the specific requirements of security via the Arm TrustZone or Intel SGX platforms.
- Weakness: Microprocessors were never envisioned to be running the mixture of very secure code or data alongside rich open operating systems. This mix has led to attacks where malware apps can interact with, or intercept, critical applications such as banking or secure login, and further creates strong business issues for applications such as bring your own device (BYOD) where malware may impact critical data services or steal trade secrets.
Additional issues come about in the cases of managing devices or biometric data types. For example, to manage a handset under a subscription agreement there is the need to introduce a separate SIM device to hold the certificates and applications that bind the phone to the network. Similarly, with biometric fingerprints there are major privacy issues relating to any leakage of these, since we only have ten fingerprints each. To solve these security challenges requires a physically tamper-resistant store for the data, something which is not only immune to software attacks, but is also highly resistant to physical probing.
Hardware-based security is essential
Building trust between IoT devices is the first step in a holistic strategy. IoT devices need strong protection for tamper-resistance. This degree of protection cannot be provided by software alone – it needs hardware-based security at the level of the three processor hardware categories outlined above.
It is important that the cost of security is as small as possible to provide lightweight solutions and to limit unaffordable impacts on the end device and service costs. To achieve this, the fundamental silicon chips and underlying intellectual property must contribute strong security features that can be exposed upwards to OEMs and system integrators.
Many critical devices need to be serviceable for ten to 20 years. These include delivering upgrades and patches remotely, support of anti-malware over long timescales, and general support of devices over a longer period than traditionally experienced, all of which require substantial security frameworks to be implemented.
Vendors must be able to demonstrate that their device operates correctly via industry- or self-certification and prove that the device was protected against reprogramming or wilful misuse. In both cases this requires protection of core functionality and proof that the device is protected, both ultimately relying on a robust security foundation.
IoT SECURITY What does this all mean?
These and other issues arising from our research lead to the following being some of the key pointers towards an IoT security strategy:
- Security is fundamental in enabling all of the value of the system, device or gadget to be realized. It should not be viewed as a cost burden – it is a value enabler. This means that a security solution should be optimised for IoT devices and use cases and assist in overcoming typical business and operational challenges.
- Security must become a number one priority to be integrated from the beginning – it must be designed-in from the start. It cannot be added later as an afterthought.
- Building trust between IoT devices is the first step in a holistic strategy. IoT devices need strong protection for tamper-resistance. This degree of protection cannot be provided by software alone – it needs hardwarebased security.
- Consistent with this, it is important that the cost of security be as small as possible to provide lightweight solutions and to limit unaffordable impacts on the end device and service costs. To achieve this, the fundamental silicon chips and underlying intellectual property must contribute strong security features that can be exposed upwards to OEMs and systems integrators.
- Many critical devices need to be serviceable for ten to 20 years. These include delivering upgrades and patches remotely, support of anti-malware over long timescales, and general support of devices over a longer period than traditionally experienced, all of which require substantial security frameworks to be implemented.
- Vendors must be able to demonstrate that their device operates correctly via industry- or self-certification and prove that the device was protected against reprogramming or wilful misuse. In both cases this requires protection of core functionality and proof that the device is protected, both ultimately relying on a robust security foundation.
Leave a Reply