Security can be a never-ending saga—a chronicle of increasingly sophisticated attacks, volumes of alerts, and long resolution timeframes where today’s Security Information and Event Management (SIEM) products can’t keep pace. SecOps teams are inundated with a very high volume of alerts and spend far too much time in tasks like infrastructure set up and maintenance. […]
How Secure Are The Most Popular Mobile Payment Methods?
As technology gets increasingly more advanced, things become smaller and easier to access than ever before — including our shopping and spending habits. The switch from using physical cash first moved to payments through checks before onward to credit cards. Now we process payments entirely online with a series of numbers without ever taking a […]
Trump and Huawei exert opposing pressures on US allies’ 5G telecom investments
THE WEEK IN 5G – The ding dong battle over the acceptability, or otherwise, of Huawei’s involvement in national 5G infrastructure projects is intensifying, says Jeremy Cowan. Security concerns have led to reservations about (or blanket rejections of) Huawei’s involvement in critical infrastructure. Grave concerns have now been expressed by countries including the USA and Australia. While a more […]
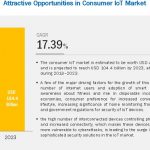
How consumer IoT demand in electronics, smart home and healthcare is growing with new tech to 2023
The Consumer Internet of Things is the network of consumer devices used in various end-applications, such as smart homes, healthcare, and consumer electronics. The consumer IoT market is estimated to be valued US$46.8 billion (€41.3 billion) by 2018 and is projected to reach US$104.4 billion (€92.1 billion) by 2023, at a CAGR of 17.39% during […]
Food for thought: How much of IoT is too much?
Recently I attended an IoT conference, says Vivart Kapoor, where three presentations caught my attention. Presentation 1: Development of IoT This presentation was held by an IoT expert representing a renowned IT company. He proudly spoke about pioneering IoT projects his company is working on: A smart house, equipped with sensors from sofa to the main […]
How Azure Security Center helps you protect your environment from new vulnerabilities
Recently the disclosure of a vulnerability (CVE-2019-5736) was announced in the open-source software (OSS) container runtime, runc. This vulnerability can allow an attacker to gain root-level code execution on a host. Runc is the underlying container runtime underneath many popular containers. Azure Security Center can help you detect vulnerable resources in your environment within Microsoft […]
Security in IoT devices relies on sustained, pervasive attention to detail across the entire threat surface
Cyber-threats are growing every day and what traditionally was seen as a data protection issue in the IT domain is becoming an increasing reality in the machine-to-machine (M2M) domain. Compounding this rise in capability is the rapid growth of the Internet of Things (IoT), writes Robin Duke-Woolley, the chief executive of Beecham Research. In this […]
IoT is on track to eat the mobile world. How?
There are a few analysts who seem to be excited about the Internet of Things’ (IoT) potential, while others have argued that it is overhyped. The advent of new technology has changed the way humans interact with machines and vice versa. From desktop websites to mobile apps, says Charles Richards, business analyst at TatvaSoft UK, the world […]
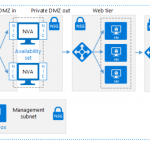
Best practices to consider before deploying a network virtual appliance
A network virtual appliance (NVA) is a virtual appliance primarily focused on network functions virtualization. A typical network virtual appliance involves various layers four to seven functions like firewall, WAN optimizer, application delivery controllers, routers, load balancers, IDS/IPS, proxies, SD-WAN edge, and more. While the public cloud may provide some of these functionalities natively, it […]
Fit and forget: The threat posed by unconfigured IoT
The march of ‘smart’ technology has seen every conceivable device in our homes and offices ‘enhanced’ with some form of connectivity. While this offers additional functionality for some, says Ken Munro, partner at Pen Test Partners, for others these smart enhancements are surplus to requirement. After all, why wirelessly connect your washing machine if you’re happy to use […]